With AI Reshaping Entry-Level Cyber, What Happens to the Security Talent Pipeline?
Editor’s Note: This post originally appeared on DarkReading, written by Joan Goodchild
Artificial intelligence (AI) is doing exactly what security teams hoped it would do: eliminate the repetitive, low-value work that has long burned out junior analysts. But in solving this problem, it may be creating another one that could have a long-lasting impact.
Log review. Alert triage. Drift detection. Basic investigation. These tasks were how generations of defenders traditionally learned the cybersecurity trade — how they built intuition, pattern recognition, and the "muscle memory" that senior leaders rely on during times of crisis. Now that AI is absorbing the grind, some say organizations risk accelerating efficiency at the cost of developing foundational expertise.
The result is an emerging paradox. AI is elevating today's analysts, yet it may leave tomorrow's leaders without the hands-on experience they need. As Visa CISO Subra Kumaraswamy notes, even with AI doing the repetitive work, teams still have to learn about "the art and science of defense."
That raises the strategic question security leaders now face: If automation is taking over the grunt work, who trains the next generation of defenders? Continue on DarkReading
Artificial intelligence (AI) is doing exactly what security teams hoped it would do: eliminate the repetitive, low-value work that has long burned out junior analysts. But in solving this problem, it may be creating another one that could have a long-lasting impact.
In many organizations, the next generation of cybersecurity experts is already in the building. IT, compliance and operations staff often have the foundational knowledge to transition into security roles with the right support. Yet, companies frequently default to external hiring, overlooking people who already understand their systems, data and culture.
Check out these Black Friday and Cyber Monday (2024) deals on your favorite cybersecurity / infosec gear and training, including TCM Security, hak5, Protonmail, and more.
“Despite its toy-like looks, this pocket-friendly multitool can be used for all kinds of hacking and penetration testing. It gives anyone an easy way to interact with the invisible waves that surround us, whether they’re RFID, NFC, Bluetooth, wifi, or radio. Think of it as a hacker Swiss army knife that you can buy for less than… “Continue Reading on Lifehacker
C-Suite & Senior Cybersecurity Executives gathered at Cipriani’s on Wall Street to discuss emerging threats and solutions in cyberspace, as part of the Official Cybersecurity Summit.
Developers, engineering leaders, and technology infrastructure professionals met at City Winery in New York City as part of Unscripted — the modern software delivery conference, hosted by Harness
Cybersecurity professionals, investors, and entrepreneurs gathered at The Yard — a co-working space in Midtown — to hear HacWare Founder and CEO, Tiffany Ricks discuss her enrerpreneurial journey into the world of cybersecurity.
Hundreds of members of the cybersecurity community gathered at the Tampa Theater in Tampa, Florida to celebrate the national premiere of the Do We Belong Here documentary, produced by Cyber Florida, and based on the podcast of the same name. Do We Belong Here highlights the stories of women in cybersecurity, showcasing their challenges and triumphs.
Cybersecurity professionals and business leaders across New York City gathered at Convene in Midtown for HackerOne’s Security@ Conference. The event, which is part of a global tour, brought together security practitioners for an evening of networking, discussions.
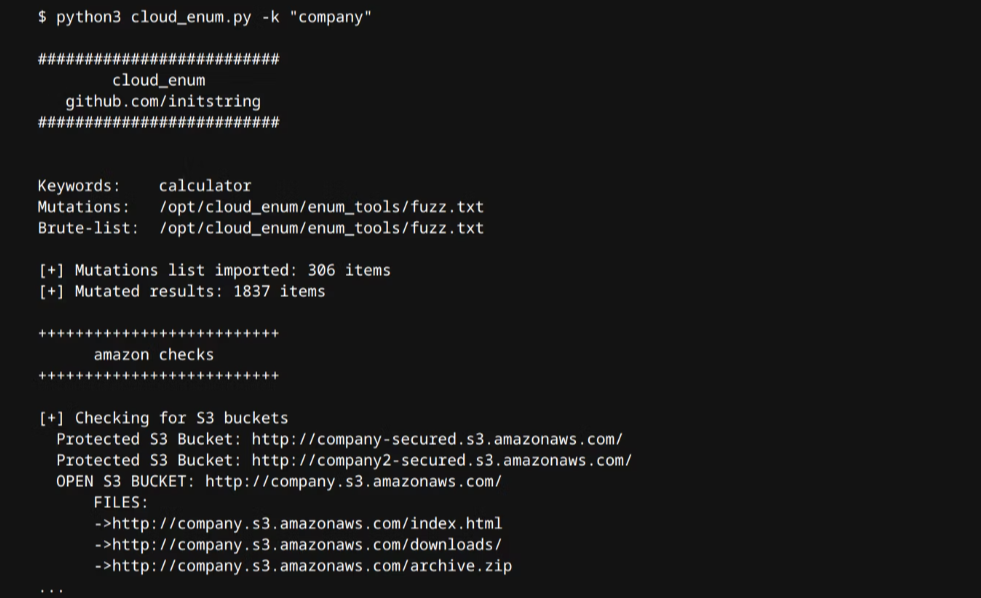
Want to get started as a security researcher and hunt bug bounties? This detailed guide by NOVASECIO, available on the bug bounty platform Intigriti, shows researchers how to discover misconfigured AWS Simple Storage Service (S3) buckets.
Thousands of cybersecurity enthusiasts recently gathered at the Metopolitan Pavilion in Chelsea for Cybertech NYC, which describes itself as 'The Main Forum for Technology Leaders and Investors in Cybersecurity & AI’.
Students and aspiring cybersecurity professionals often ask: “Do I need to know programming to work in cybersecurity?“ Here’s the answer.
Cybersecurity training organization, OffSec recently announced a new entry-level cybersecurity course and credential, the OffSec CyberCore Certification and its accompanying course, SEC-101: Cybersecurity Essentials. The course covers Windows and Linux basics, Python Scripting, Networking, Powershell, Data Transformation, as well as Frameworks and Standards, and other in-demand security related skills.
A recent article from an anonymous author, ‘Chadly McCyberton’, claims that cybersecurity jobs no longer exist, encourages job seekers to give up. We’re not okay with that.
picoCTF, a cybersecurity Capture The Flag (CTF) competition created and run by Carnegie Mellon University's CyLab Security and Privacy Institute in 2013, is now the largest high school hacking competition in the world.
Artificial Intelligence is changing the way we work. Here’s how cybersecurity students and professionals can learn the skills required to defend AI Systems. Here’s our guide to navigating the world of AI for cybersecurity professionals.
This first of its kind Cybersecurity Training Ecosystem Map, published by AccessCyber, identifies and highlights key organizations preparing professionals for careers in security.
"This looks good... but you're not actually going to teach them how to hack, are you?" The head of the Computer Science department asks, almost in a whisper, as if she had said a 'bad' word. I had just pitched a cybersecurity course to a major university. They liked it, mostly... except for the title: Ethical Hacking.